|
coreboot
coreboot is an Open Source project aimed at replacing the proprietary BIOS found in most computers.
|
 |
coreboot
coreboot is an Open Source project aimed at replacing the proprietary BIOS found in most computers.
|
#include <security/vboot/antirollback.h>#include <security/vboot/tpm_common.h>#include <security/tpm/tspi.h>#include <security/tpm/tss.h>#include <security/tpm/tss/tcg-1.2/tss_structures.h>#include <security/tpm/tss/tcg-2.0/tss_structures.h>#include <vb2_api.h>#include <console/console.h>
Go to the source code of this file.
Macros | |
| #define | VBDEBUG(format, args...) printk(BIOS_INFO, "%s():%d: " format, __func__, __LINE__, ## args) |
| #define | RETURN_ON_FAILURE(tpm_cmd) |
Functions | |
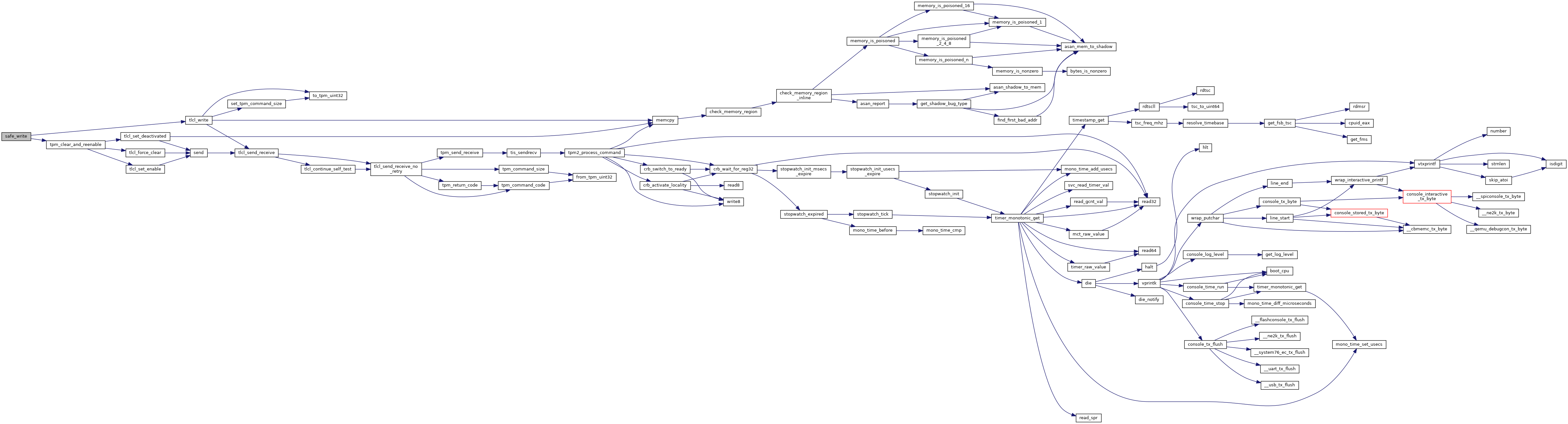
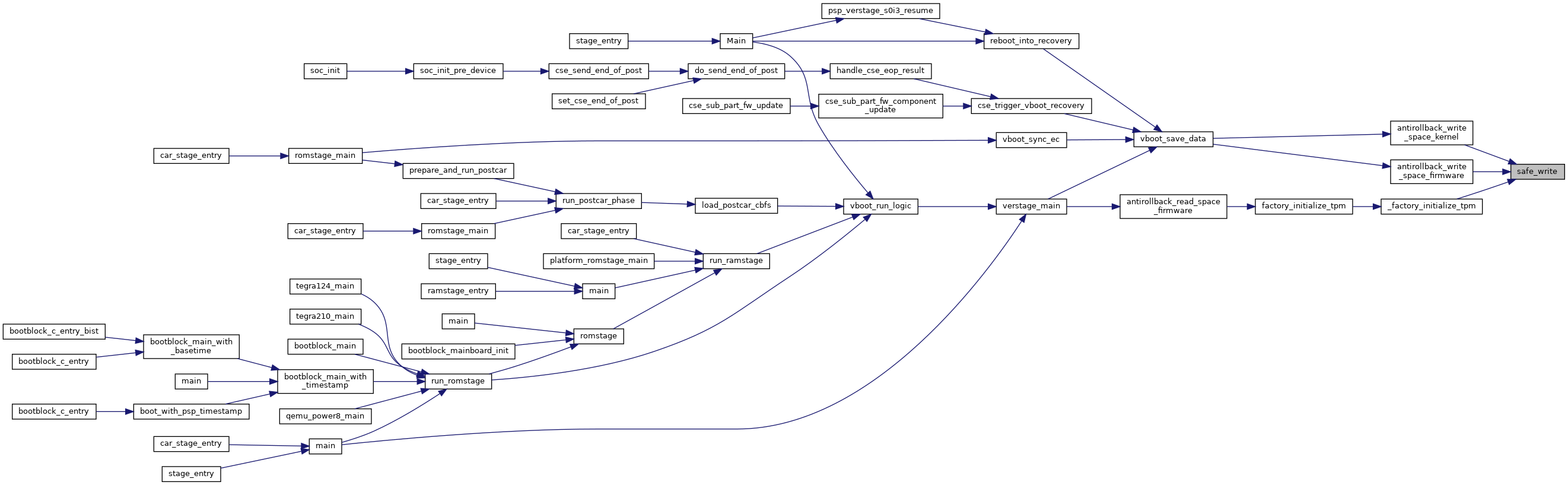
| static uint32_t | safe_write (uint32_t index, const void *data, uint32_t length) |
| Like tlcl_write(), but checks for write errors due to hitting the 64-write limit and clears the TPM when that happens. More... | |
| static uint32_t | read_space_firmware (struct vb2_context *ctx) |
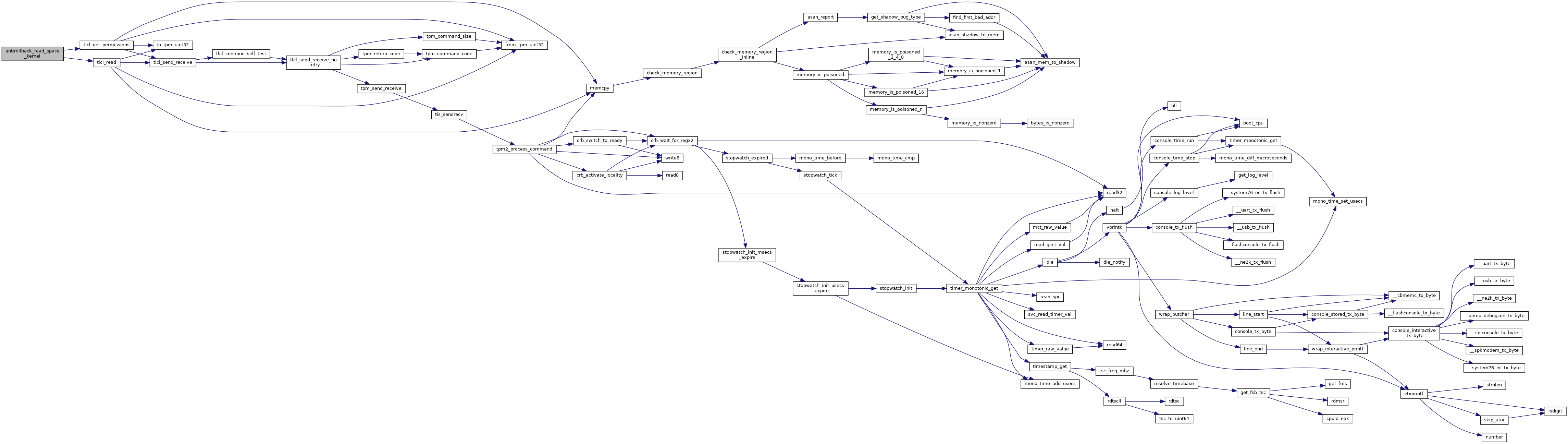
| uint32_t | antirollback_read_space_kernel (struct vb2_context *ctx) |
| Read and write kernel space in TPM. More... | |
| static uint32_t | safe_define_space (uint32_t index, uint32_t perm, uint32_t size) |
| Similarly to safe_write(), this ensures we don't fail a DefineSpace because we hit the TPM write limit. More... | |
| static uint32_t | _factory_initialize_tpm (struct vb2_context *ctx) |
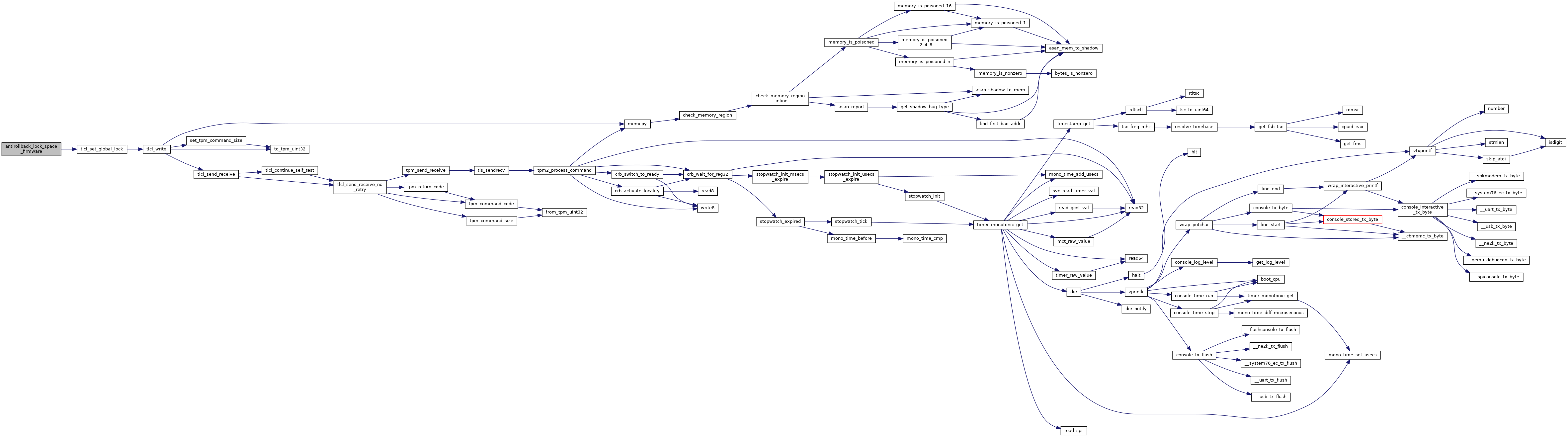
| uint32_t | antirollback_lock_space_firmware (void) |
| Lock must be called. More... | |
| static uint32_t | factory_initialize_tpm (struct vb2_context *ctx) |
| Perform one-time initializations. More... | |
| uint32_t | antirollback_read_space_firmware (struct vb2_context *ctx) |
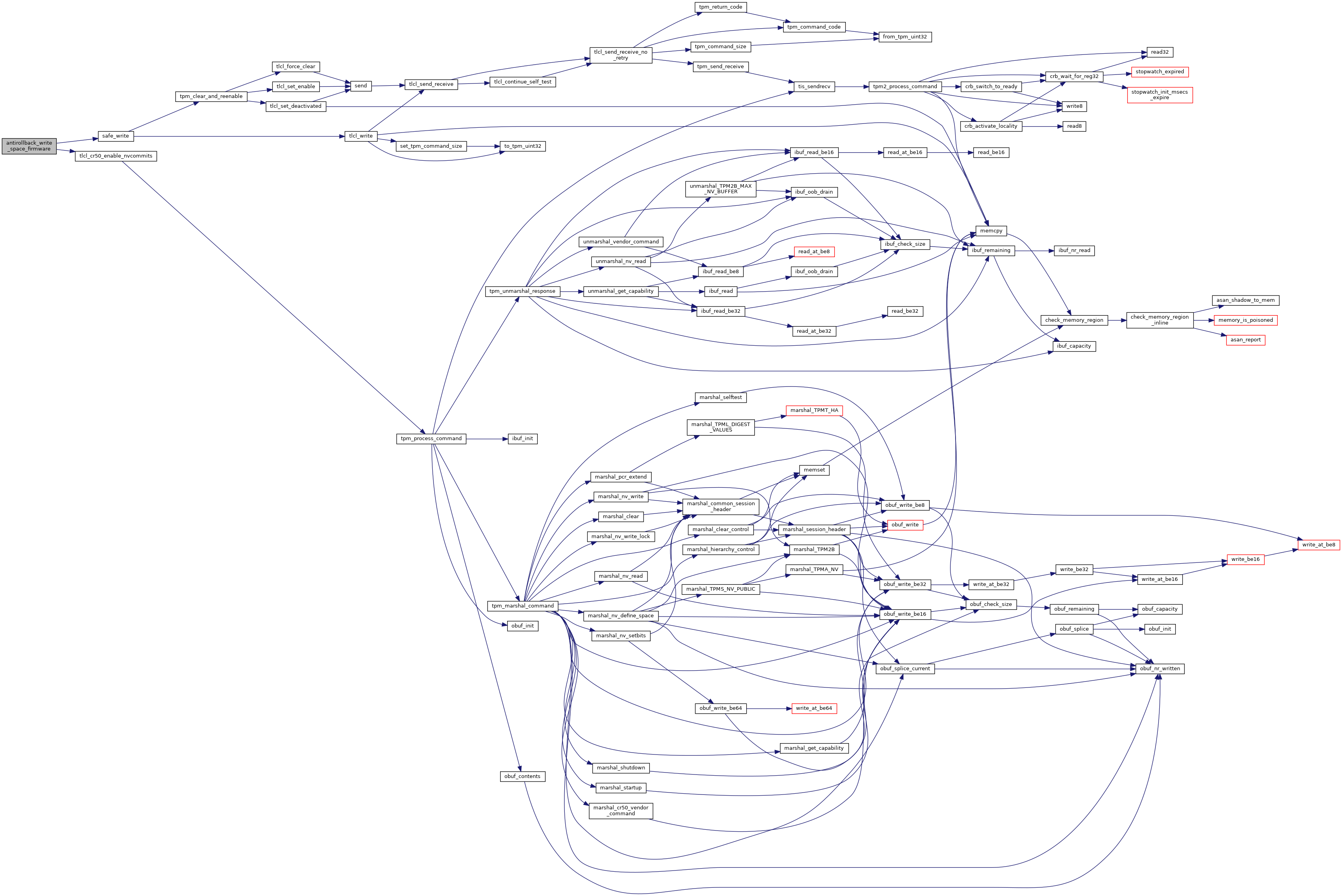
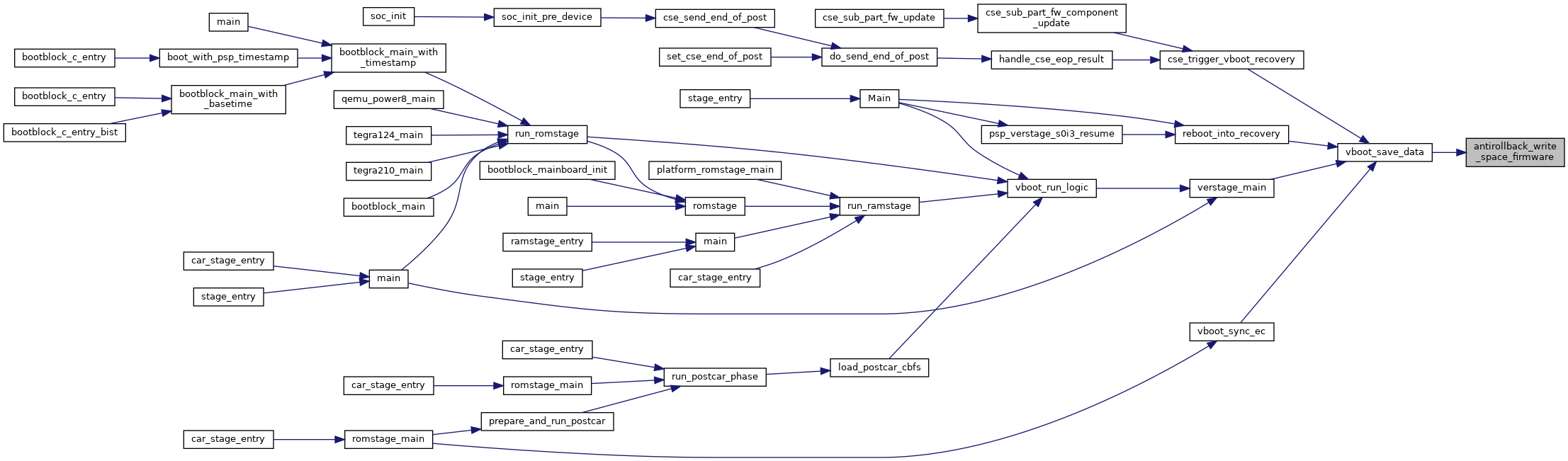
| uint32_t | antirollback_write_space_firmware (struct vb2_context *ctx) |
| Write may be called if the versions change. More... | |
| uint32_t | antirollback_write_space_kernel (struct vb2_context *ctx) |
| vb2_error_t | vb2ex_tpm_clear_owner (struct vb2_context *ctx) |
| #define RETURN_ON_FAILURE | ( | tpm_cmd | ) |
Definition at line 20 of file secdata_tpm.c.
| #define VBDEBUG | ( | format, | |
| args... | |||
| ) | printk(BIOS_INFO, "%s():%d: " format, __func__, __LINE__, ## args) |
Definition at line 17 of file secdata_tpm.c.
|
static |
Definition at line 486 of file secdata_tpm.c.
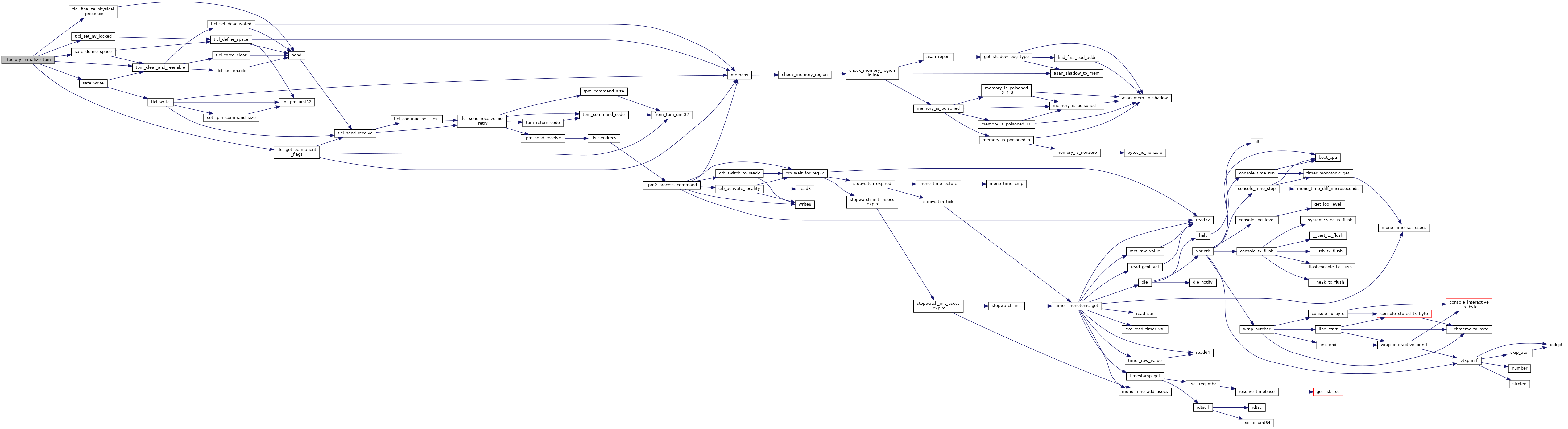
References FIRMWARE_NV_INDEX, KERNEL_NV_INDEX, tdTPM_PERMANENT_FLAGS::nvLocked, tdTPM_PERMANENT_FLAGS::physicalPresenceLifetimeLock, RETURN_ON_FAILURE, safe_define_space(), safe_write(), tlcl_finalize_physical_presence(), tlcl_get_permanent_flags(), tlcl_set_nv_locked(), tpm_clear_and_reenable(), TPM_NV_PER_GLOBALLOCK, TPM_NV_PER_PPWRITE, TPM_SUCCESS, and VBDEBUG.
Referenced by factory_initialize_tpm().
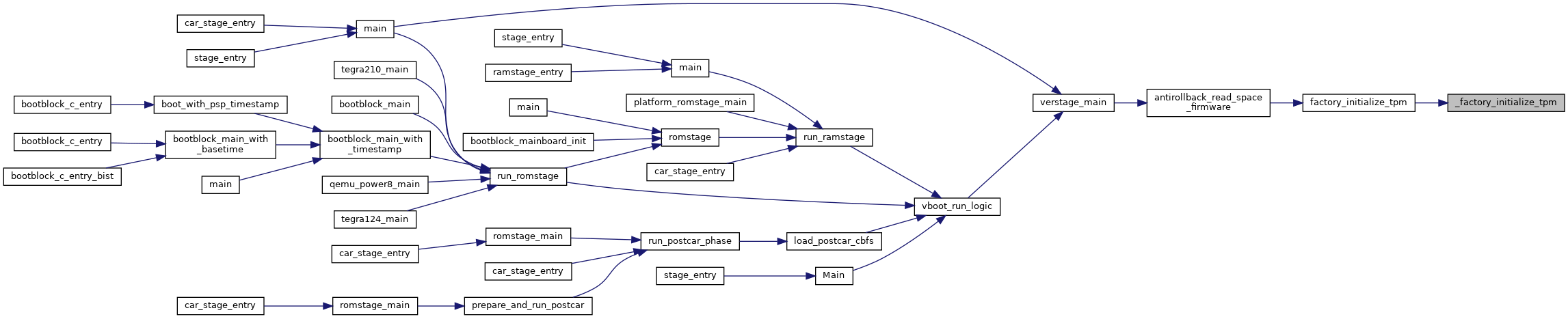
Lock must be called.
Definition at line 543 of file secdata_tpm.c.
References tlcl_set_global_lock().
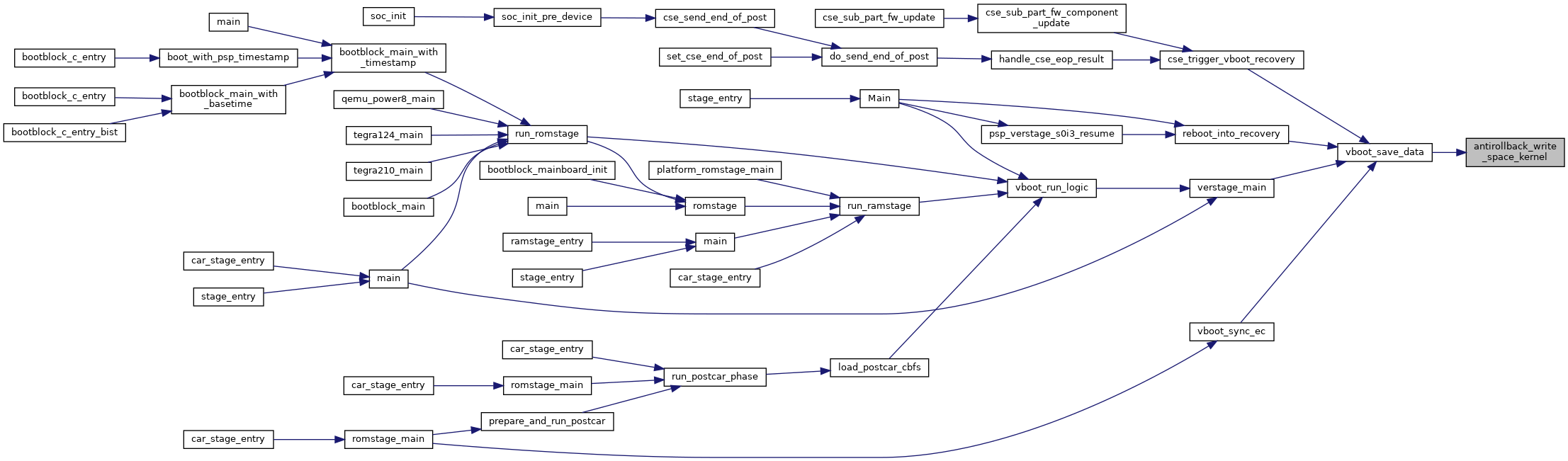
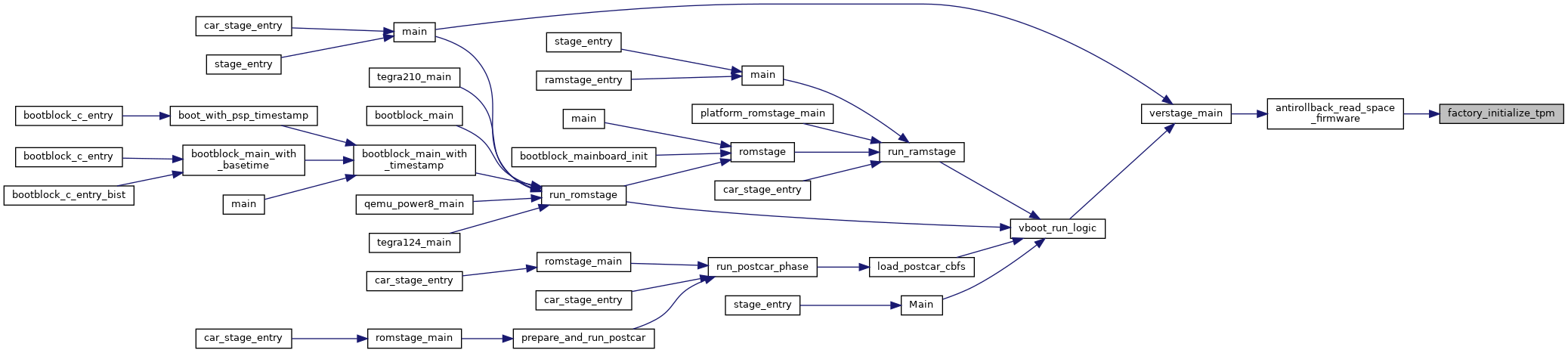
Referenced by verstage_main().
| uint32_t antirollback_read_space_firmware | ( | struct vb2_context * | ctx | ) |
Definition at line 595 of file secdata_tpm.c.
References factory_initialize_tpm(), read_space_firmware(), RETURN_ON_FAILURE, TPM_E_BADINDEX, TPM_E_CORRUPTED_STATE, TPM_SUCCESS, and VBDEBUG.
Referenced by verstage_main().
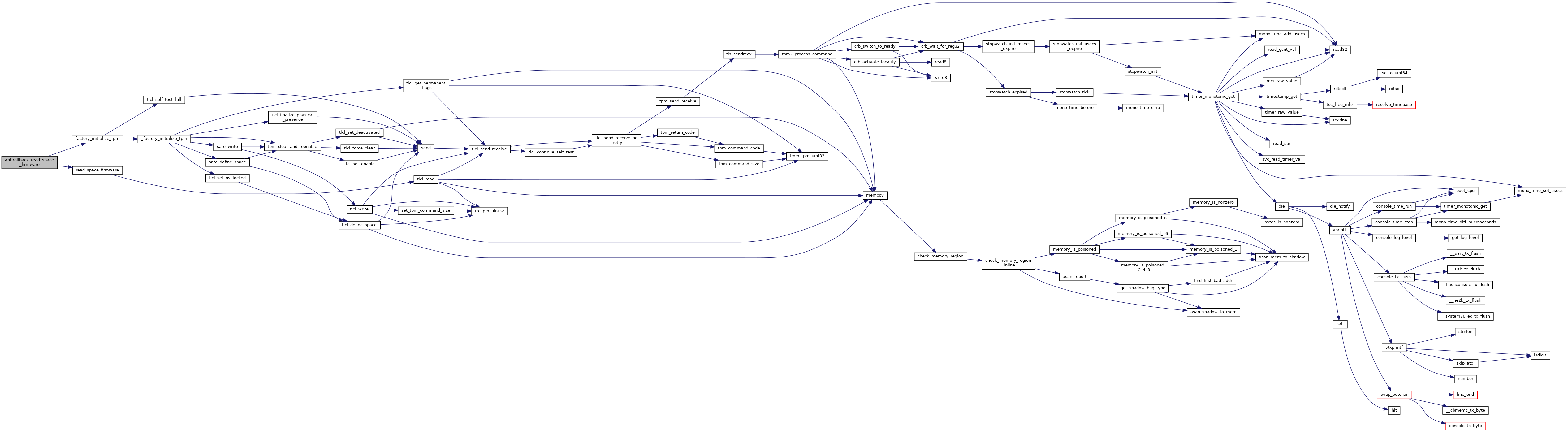
| uint32_t antirollback_read_space_kernel | ( | struct vb2_context * | ctx | ) |
Read and write kernel space in TPM.
Definition at line 39 of file secdata_tpm.c.
References BIOS_ERR, CONFIG, KERNEL_NV_INDEX, printk, RETURN_ON_FAILURE, tlcl_get_permissions(), tlcl_read(), TPM2, TPM_E_CORRUPTED_STATE, TPM_E_RANGE, TPM_NV_PER_PPWRITE, TPM_SUCCESS, and VBDEBUG.
Referenced by verstage_main().
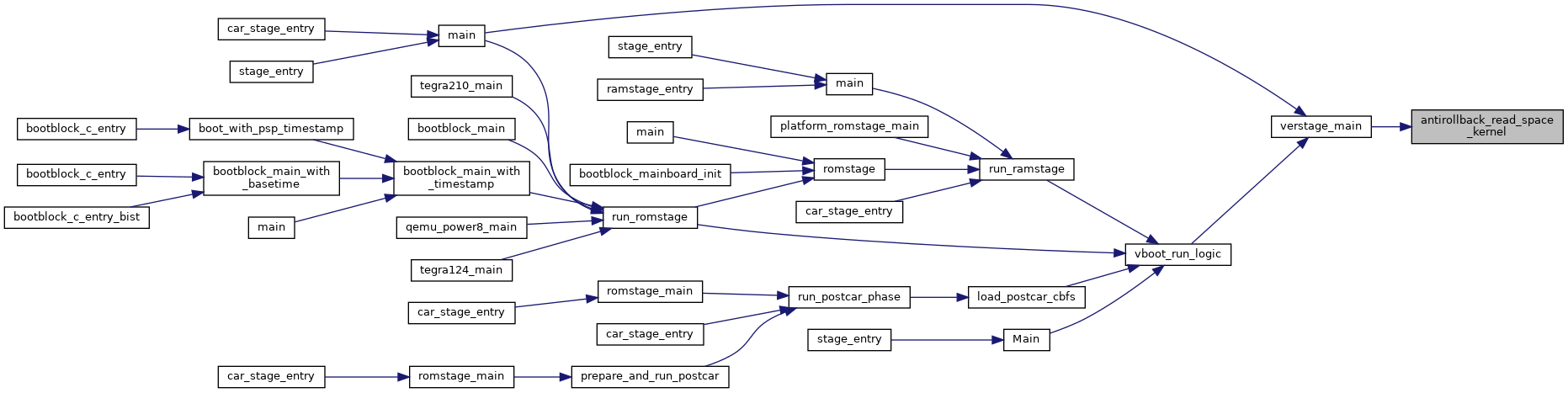
| uint32_t antirollback_write_space_firmware | ( | struct vb2_context * | ctx | ) |
Write may be called if the versions change.
Definition at line 613 of file secdata_tpm.c.
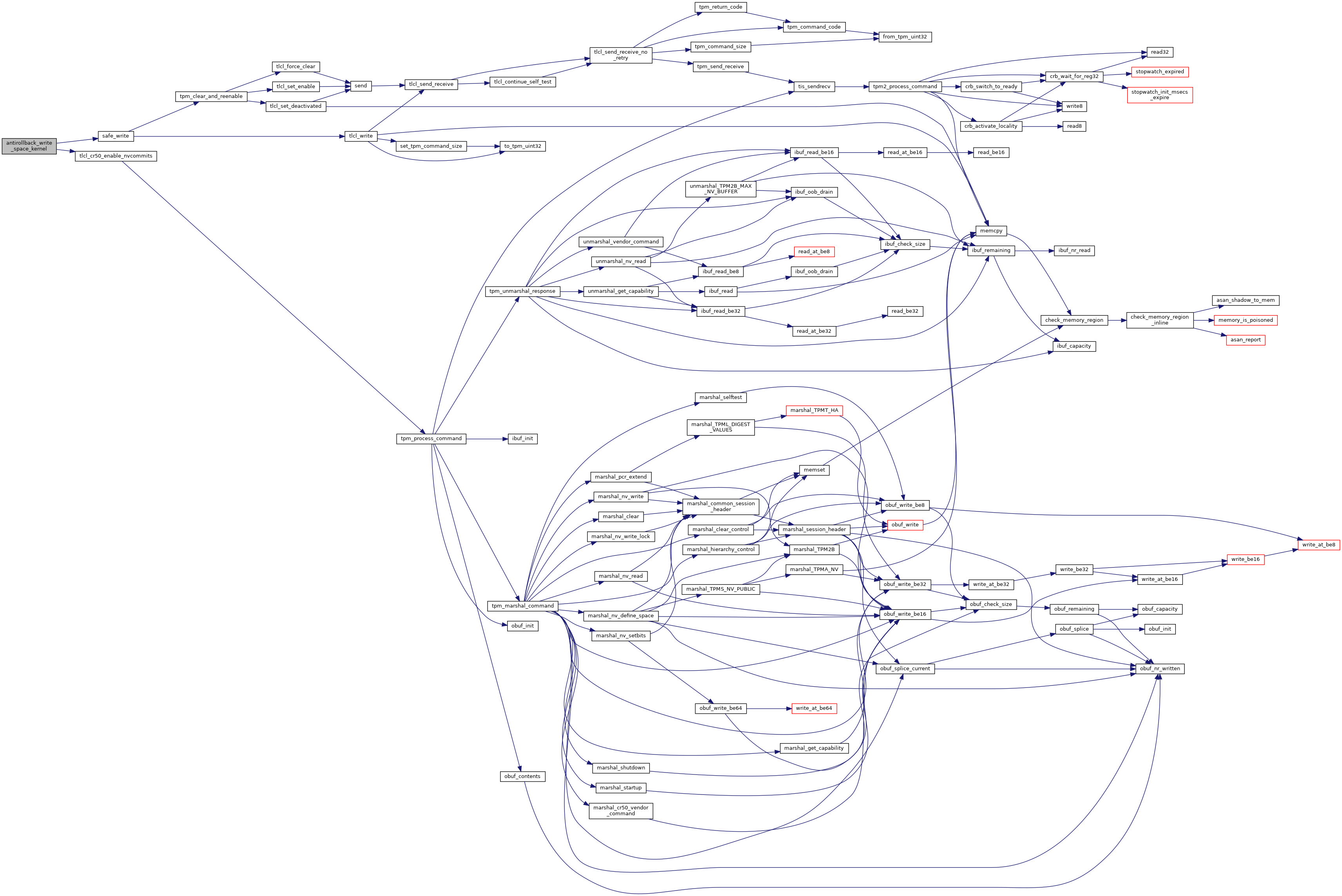
References CONFIG, FIRMWARE_NV_INDEX, safe_write(), and tlcl_cr50_enable_nvcommits().
Referenced by vboot_save_data().
| uint32_t antirollback_write_space_kernel | ( | struct vb2_context * | ctx | ) |
Definition at line 621 of file secdata_tpm.c.
References CONFIG, KERNEL_NV_INDEX, safe_write(), and tlcl_cr50_enable_nvcommits().
Referenced by vboot_save_data().
|
static |
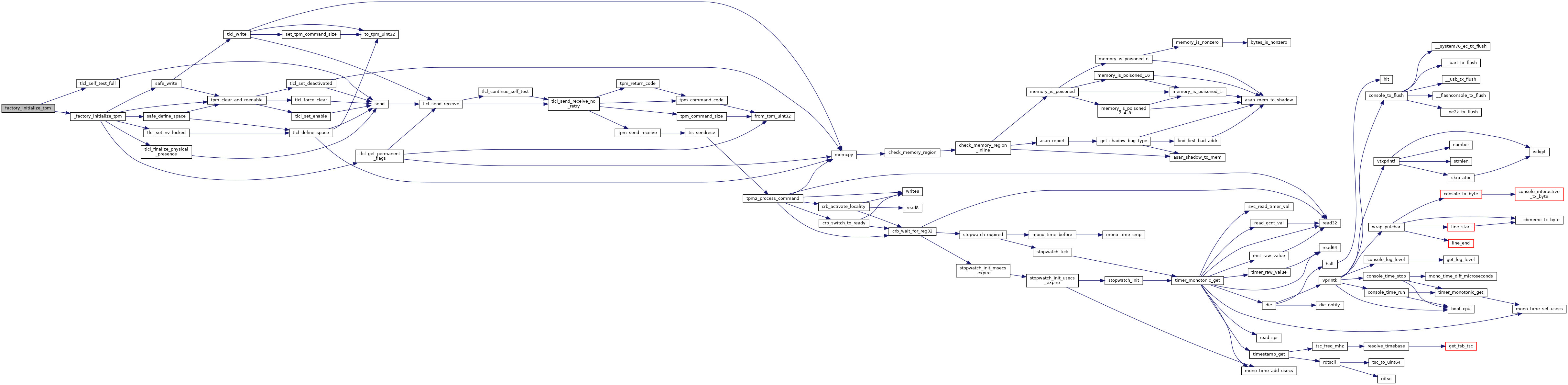
Perform one-time initializations.
Create the NVRAM spaces, and set their initial values as needed. Sets the nvLocked bit and ensures the physical presence command is enabled and locked.
Definition at line 557 of file secdata_tpm.c.
References _factory_initialize_tpm(), tlcl_self_test_full(), TPM_SUCCESS, and VBDEBUG.
Referenced by antirollback_read_space_firmware().
|
static |
Definition at line 31 of file secdata_tpm.c.
References FIRMWARE_NV_INDEX, RETURN_ON_FAILURE, tlcl_read(), and TPM_SUCCESS.
Referenced by antirollback_read_space_firmware().
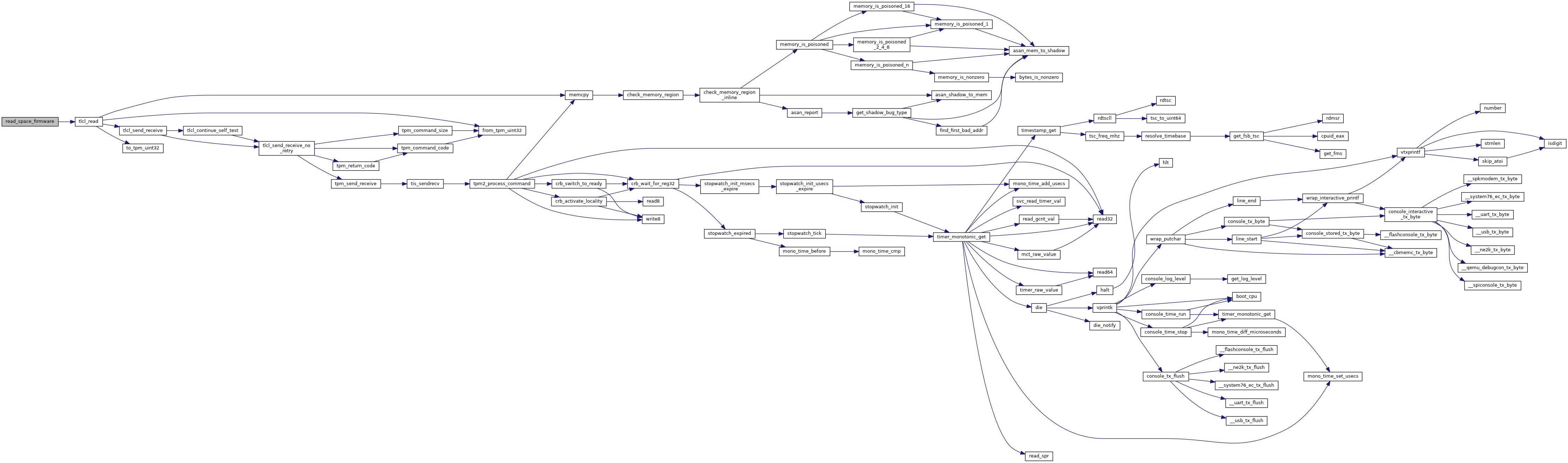
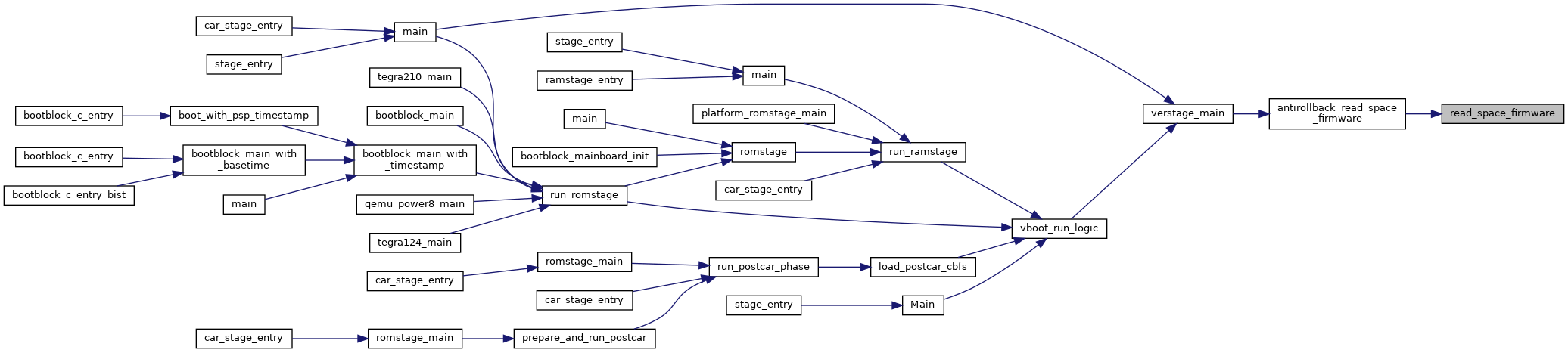
Similarly to safe_write(), this ensures we don't fail a DefineSpace because we hit the TPM write limit.
This is even less likely to happen than with writes because we only define spaces once at initialization, but we'd rather be paranoid about this.
Definition at line 475 of file secdata_tpm.c.
References RETURN_ON_FAILURE, tlcl_define_space(), tpm_clear_and_reenable(), and TPM_E_MAXNVWRITES.
Referenced by _factory_initialize_tpm().
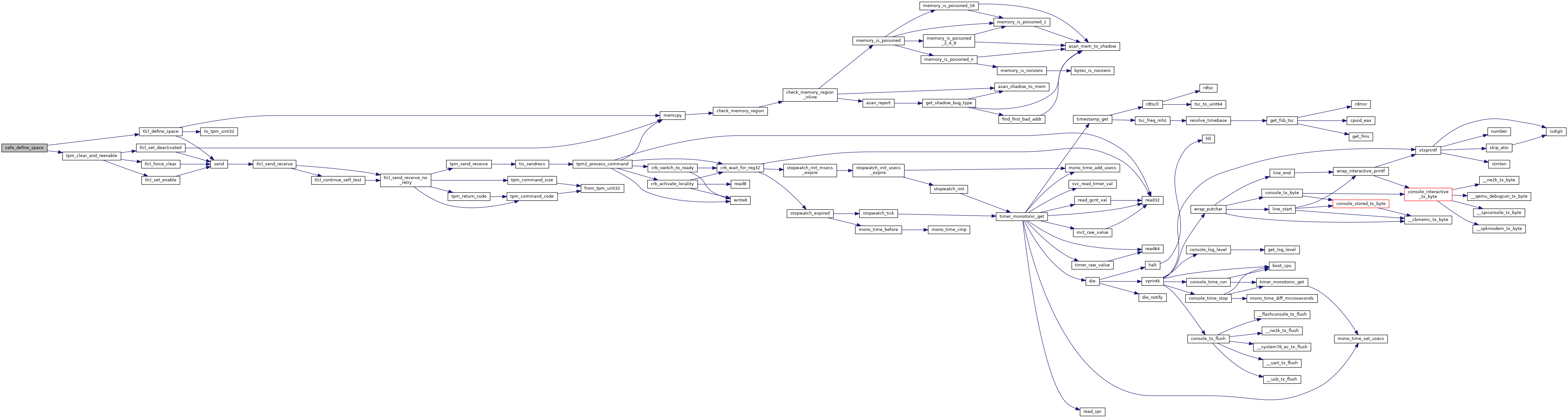
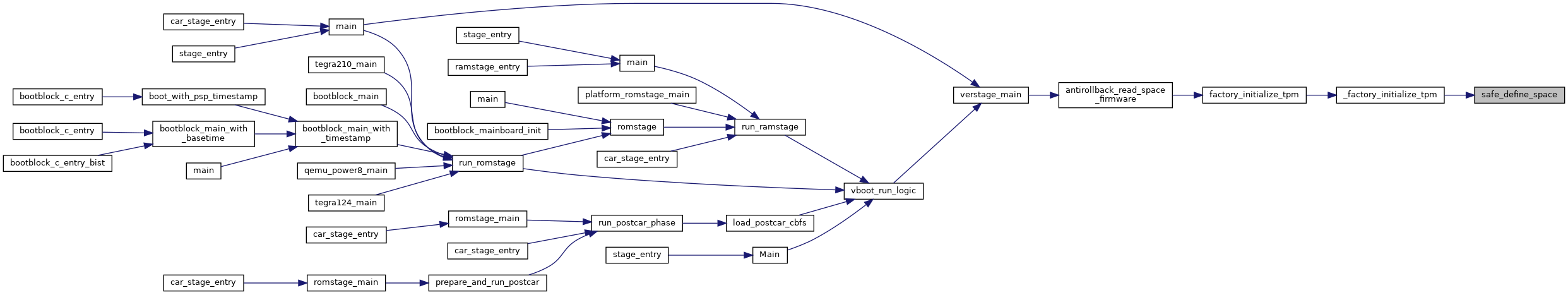
Like tlcl_write(), but checks for write errors due to hitting the 64-write limit and clears the TPM when that happens.
This can only happen when the TPM is unowned, so it is OK to clear it (and we really have no choice). This is not expected to happen frequently, but it could happen.
Definition at line 458 of file secdata_tpm.c.
References length, RETURN_ON_FAILURE, tlcl_write(), tpm_clear_and_reenable(), and TPM_E_MAXNVWRITES.
Referenced by _factory_initialize_tpm(), antirollback_write_space_firmware(), and antirollback_write_space_kernel().
| vb2_error_t vb2ex_tpm_clear_owner | ( | struct vb2_context * | ctx | ) |
Definition at line 640 of file secdata_tpm.c.
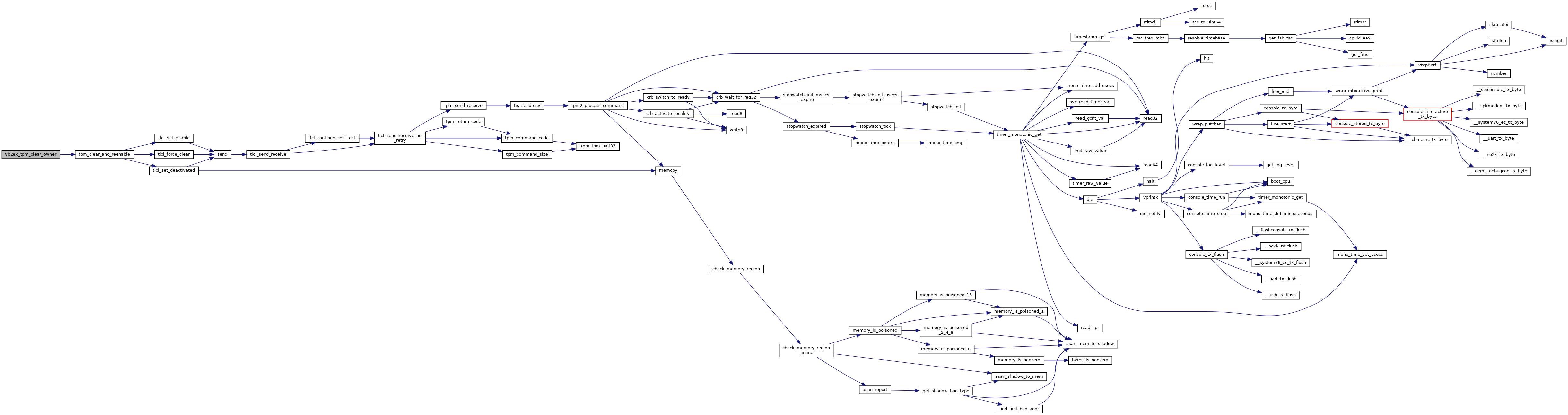
References BIOS_INFO, printk, and tpm_clear_and_reenable().